Cloud computing may not be as secure as you would like to believe…Vulnerabilities in Azure Part 2
As promised this is Part 2… Otherwise known as “How to Hack Windows Azure”…
The information in this post was obtained through public sources, no computers were compromised nor hacked into to obtain this information. You too can obtain everything listed in this article in a matter of minutes using free software.
In this post I will show you how UNSECURE Windows Azure really is…
Using a freshly made Server 2008R2 server residing in Windows Azure, you can find everything you need to start gathering information!
I will give you a little background… When you spin up your fresh newly created Virtual Machine in Windows Azure, you are given the option to “Choose your Region”. These regions are where the server farms that comprise Windows Azure are located. You are given the options of : North Europe, West Europe, East US, West US, Southeast Asia and East Asia.
What you need to realize is the following:
A. Whatever you name your new Virtual Machine becomes your VMs computer name. This also becomes “YourVMname.cloudapp.net”. I will show you why this is significant later…
B. The region that you select for your VM, those regions break down as follows:
North Europe = europenorth.internal.cloudapp.net
West Europe = europewest.internal.cloudapp.net
East US = useast.internal.cloudapp.net
West US = uswest.internal.cloudapp.net
Southeast Asia = asiasoutheast.internal.cloudapp.net
East Asia = asiaeast.internal.cloudapp.net
Internal.cloudapp.net = 70.37.50.25
This isn’t too complicated to figure this out. If you are already inside of Windows Azure, then you would be able to use this information to gather more information about servers, connections and virtual machines that reside on these servers. (I showed you this in Part 1)
Now here comes what you have been waiting for…
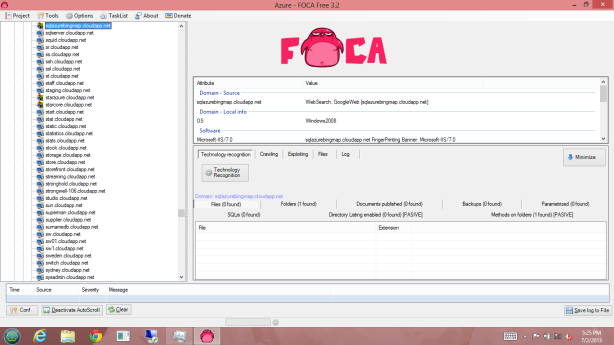
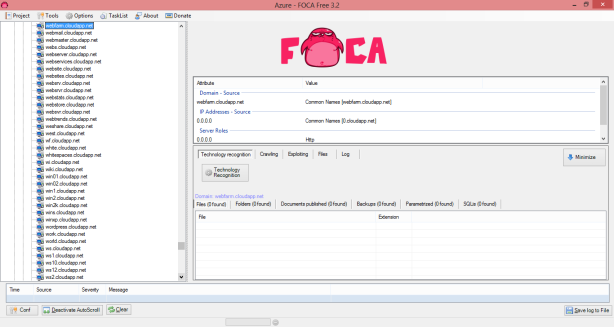
Using a computer that was NOT connected to Windows Azure, I was able to run the program Foca 3.2 to gather information about Windows Azure.
FOCA Free 3.2 is a tool for performing fingerprinting processes and information gathering in web audit work. Free version performs search servers, domains, URLs and documents published, and the discovery of software versions on servers and clients. FOCA became famous for metadata extraction on public documents, but today is much more than that.
I used the domain name “cloudapp.net” for this Foca 3.2 search.
After an hour I had discovered IP Address’, Virtual Machine Names, and even vulnerabilities listed on virtual machines with very little effort.
What does this mean to a “hacker”? Well it gives the “hacker” a lot of information to exploit…
In an hour I found 444 Servers in Windows Azure with IP address, websites hosted in Windows Azure, virtual machine names, as well as vulnerabilities of some of those hosted servers in Windows Azure.
I will let the following screenshots speak for themselves…
As you can see in this article…Windows Azure is not safe from “hackers”… With one free program, and a little time, you can easily find targets to exploit.
In Part 1, I communicated with Microsoft for two months. Microsoft told me via email that my discovery was legitimate, then after two months (plenty of time to fix the issue) Microsoft stated that they have measures that prevent the MITM and DOS attacks. The tool shown in this article FOCA 3.2 on the other hand can not be patched by Microsoft.
This article is designed to show you how “UNSECURE” that Windows Azure actually is. Like I said in Post 1, I would not host my virtual machines in Windows Azure, except for “penetration testing or development”.
Imagine what would happen if someone had the “time & inclination” what they could actually exploit? Scary isn’t it!









































































Does Amazon EC2 have this same issue, or it strictly with Azure? – Just wondering how this is different that having a machine exposed to the internet. Obviously a machine that is accessible from the internet is vulnerable, regardless of the cloud service that is used.
I’ve never looked into Amazon EC2, I would imagine if you did the search against Amazon you’d find similar information.
Great article!
I have learned so much from your blog, keep up the good work!
I tried it yesterday…. dint find any servers…but found some unallocated servers… did Microsoft come up with a patch…
I believed they patched the IPv6 DDOS capabilities, after my white paper, but do not know. I no longer have an Azure account to play with. MS jerked me around after I sent them the whitepaper.
oh … ok thanks … 🙂
Thanks for your marvelous posting! I actually enjoyed reading it, you
can be a great author. I will remember to bookmark your blog and will
come back from now on. I want to encourage yourself to continue your great job, have a nice holiday weekend!
thanks for sharing. this could be a problem if some ports are opened.